
Author: Steve Meekins is a Certified Master Anaplanner and has worked in the Anaplan ecosystem for over 8 years. Steve has worked in both industry and consulting and has successfully architected over 50 end-to-end EPM implementations.
The challenge
Security management is no simple task for organizations that have several users (200 -1000+). It can be a very manual set-up and a maintenance nightmare. It is especially complicated when dealing with multiple connected spoke models across a Dev/QA/Prod landscape. With that in mind, the North Star would be to automate Anaplan security leveraging an enterprise scalable identity management and governance system and the Anaplan SCIM API.
My solution
Below is a diagram of how I architected security automation in Anaplan:
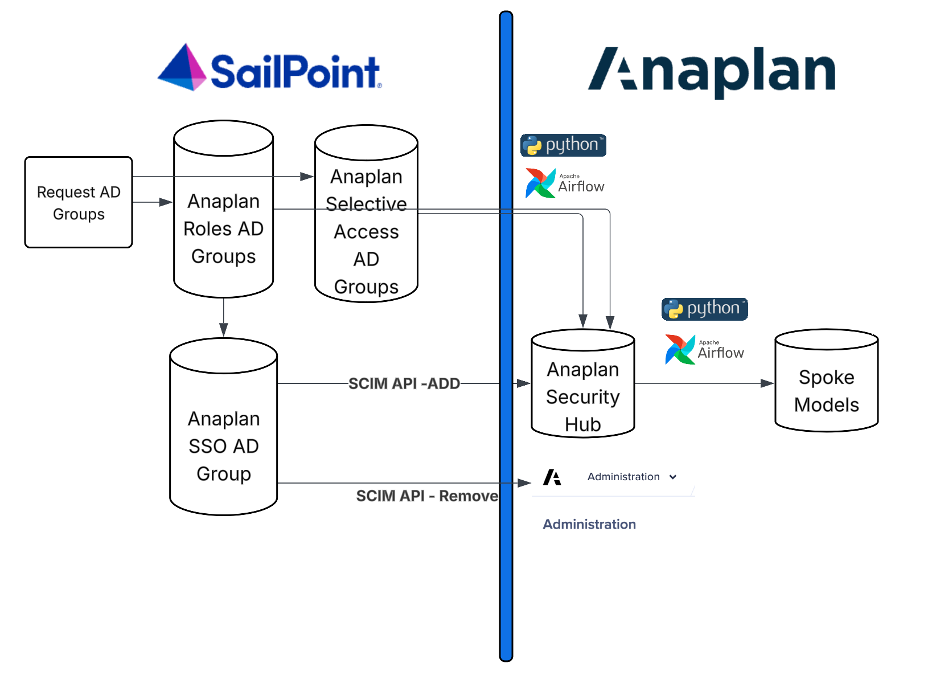
- The process for end users is straight forward. An end user logs into SailPoint and requests 1 and only 1 Anaplan role. Logic is in place to ensure that an end user can only have 1 role. Once the Anaplan Role AD request is approved, the user is automatically added to the Anaplan SSO AD group for Anaplan login. The user must also select 1 or more selective access AD groups which follow the Entity hierarchy structure in Anaplan.
https://scimapi.docs.apiary.io/
- The SCIM API runs twice a day to automatically add users to the Anaplan Security Hub with “No Access” pulling from the Anaplan SSO AD Group. This step saves manually setting up a user in Anaplan. When a user is no longer with the company, the user is automatically removed from the Anaplan SSO AD Group and the SCIM API disables/removes a user’s Anaplan access.
- Twice a day, Airflow runs a Python script-based Dag to pull Anaplan Role AD Groups and Anaplan Selective Access AD Groups and associated users into the Anaplan Security Hub Model. Within the Security Hub Model, modules have been built to determine Spoke Model access based upon Anaplan roles and Selective Access roles. User Import Views are created in the security hub and spoke import actions are created to load users to each spoke model from those views.
https://anaplan.docs.apiary.io/
- Airflow orchestrates the automatic import of users/roles/selective access from the security hub into the Anaplan spoke models as part of the Python Dag.
- The end-to-end process generally ensures that an Anaplan user is auto added to Anaplan spoke models within 2 days following the access request in SailPoint.
Security automation pros
- Simple governed process for end users to request Anaplan access.
- Initial access request in SailPoint requires appropriate levels of approvals.
- Users are automatically added to Anaplan minimizing manual efforts and errors.
- Users are automatically disabled in Anaplan when they are no longer with the company.
- Audit process within SailPoint is governed and required.
Security automation cons
- It does take a day or two before a user is added to Anaplan.
- SCIM API requires a basic authenticated user. Password does need to get reset every few months.
- Security is no longer in the hands of an Anaplan admin. Any manual changes will get written over when the API runs.
Questions? Leave a comment!